Difference between revisions of "HowTo - ssh"
(Created page with " [https://www.rootusers.com/enable-ssh-linux-mint/ How To Enable SSH in Linux Mint] Passwordless SSH = Using SSH to get stuff done = == Make it easier to connect == Don't use password authentication. Use [https://www.ssh.com/academy/ssh/public-key-authentication Public Key Authentication]. *<code>ssh-keygen</code> **(Note: You only have to do this step once on any particular machine.) **The passphrase is optional. *<code>ssh-copy-id '''user@MACHINENAME'''</code> *...") |
|||
| (13 intermediate revisions by 2 users not shown) | |||
| Line 6: | Line 6: | ||
= Using SSH to get stuff done = | = Using SSH to get stuff done = | ||
== Make it easier to connect == | == Make it easier to connect == | ||
=== Part 1: No passwords! === | |||
Don't use password authentication. Use [https://www.ssh.com/academy/ssh/public-key-authentication Public Key Authentication]. | Don't use password authentication. Use [https://www.ssh.com/academy/ssh/public-key-authentication Public Key Authentication]. | ||
| Line 14: | Line 15: | ||
**This can be done for as many remote machines as you like. | **This can be done for as many remote machines as you like. | ||
This will simplify your life. From this point on, any time you SSH into (or SCP to/from etc...) the machine known as '''MACHINENAME''' while working at the machine you've done this on, you'll be automagically authenticated. | This will simplify your life. From this point on, any time you SSH into (or SCP to/from etc...) the machine known as '''MACHINENAME''' while working at the machine you've done this on, you'll be automagically authenticated. | ||
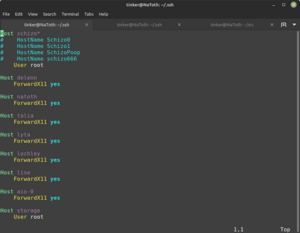
=== Part 2: ~/.ssh/config === | |||
Set up the list of machines you expect to regularly connect to. | |||
* <code>vi ~/.ssh/config</code> | |||
& set up options for the various '''Hosts''' | |||
There are a lot of things you can configure here. | |||
<span style="color: rgb(132, 63, 161);">'''<span style="font-size: 18pt;">WIP</span>'''</span> | |||
(But... An example for now...) | |||
[[File:Screenshot from 2022-11-27 00-45-29.png{{!}}300px{{!}}left{{!}}thumb{{!}}Sample ~/.ssh/config]] | |||
<div style="clear: both"></div> | |||
== Signing in to a machine == | == Signing in to a machine == | ||
| Line 20: | Line 34: | ||
*<code>ssh '''user@MACHINENAME'''</code> | *<code>ssh '''user@MACHINENAME'''</code> | ||
This will securely give you a terminal session of the remote machine. (Much like good old telnet... But not quite so sketchily insecure.) | This will securely give you a terminal session of the remote machine. (Much like good old telnet... But not quite so sketchily insecure.) | ||
('''Note:''' if the username on the remote machine is the same as on the local machine, you can leave off '''user@''' ) | |||
== Executing commands remotely == | == Executing commands remotely == | ||
Also, pretty straightforward... | Also, pretty straightforward... | ||
=== Regular Command-Line commands === | |||
*<code>ssh '''user@MACHINENAME "Command to be executed"'''</code> | *<code>ssh '''user@MACHINENAME "Command to be executed"'''</code> | ||
=== GUI (X11) commands === | |||
SSH can pass X11 windows through to remote machines. | |||
<span style="color: rgb(132, 63, 161);" >If your remote system is not already configured for X11, you'll need to log into it & install '''xauth'''.</span> | |||
*<code>sudo apt install xauth</code> | |||
As an example: Say you want to open a graphical view of the status of a server. I currently use [https://github.com/oguzhaninan/Stacer stacer] for this task. | |||
*<code>ssh -X '''user@MACHINENAME''' stacer</code> | |||
<span style="color: rgb(132, 63, 161);" >(You may have to enable X11 Forwarding...)</span> | |||
=== Priveledged Remote Commands (needing root) === | |||
If you want to execute a command remotely that requires '''sudo''', you'll have to add a '''-t''' to the command line or else '''sudo''' with tell you where to go. | If you want to execute a command remotely that requires '''sudo''', you'll have to add a '''-t''' to the command line or else '''sudo''' with tell you where to go. | ||
| Line 31: | Line 61: | ||
*<code>ssh -t '''user@MACHINENAME "Command to be executed"'''</code> | *<code>ssh -t '''user@MACHINENAME "Command to be executed"'''</code> | ||
This is because '''sudo''' intentionally will NOT run without a local terminal session. | This is because '''sudo''' intentionally will NOT run without a local terminal session. | ||
Another option is to enable root login via ssh. | |||
<span style="color: rgb(224, 62, 45);">'''WARNING!!! This may be a security risk!'''</span> | |||
*<code>vi /etc/ssh/sshd_config</code> | |||
<span style="color: rgb(224, 62, 45);">and change:</span> | |||
<code>#PermitRootLogin prohibit-password</code> | |||
<span style="color: rgb(224, 62, 45);">to:</span> | |||
<code>PermitRootLogin yes</code> | |||
== Transferring files == | == Transferring files == | ||
| Line 108: | Line 152: | ||
*[https://cormachogan.com/2016/04/13/ssh-esxi-hosts-without-providing-password/ How to SSH between ESXi 6.0U2 hosts without providing a password] | *[https://cormachogan.com/2016/04/13/ssh-esxi-hosts-without-providing-password/ How to SSH between ESXi 6.0U2 hosts without providing a password] | ||
*[https://www.tecmint.com/secure-openssh-server/ How to Secure and Harden OpenSSH Server] | *[https://www.tecmint.com/secure-openssh-server/ How to Secure and Harden OpenSSH Server] | ||
[[Category:Linux]] | |||
[[Category:LinuxTools]] | |||
Latest revision as of 13:40, 8 January 2023
How To Enable SSH in Linux Mint
Using SSH to get stuff done
Make it easier to connect
Part 1: No passwords!
Don't use password authentication. Use Public Key Authentication.
ssh-keygen- (Note: You only have to do this step once on any particular machine.)
- The passphrase is optional.
ssh-copy-id user@MACHINENAME- This can be done for as many remote machines as you like.
This will simplify your life. From this point on, any time you SSH into (or SCP to/from etc...) the machine known as MACHINENAME while working at the machine you've done this on, you'll be automagically authenticated.
Part 2: ~/.ssh/config
Set up the list of machines you expect to regularly connect to.
vi ~/.ssh/config
& set up options for the various Hosts
There are a lot of things you can configure here.
WIP
(But... An example for now...)
Signing in to a machine
Pretty straightforward:
ssh user@MACHINENAME
This will securely give you a terminal session of the remote machine. (Much like good old telnet... But not quite so sketchily insecure.)
(Note: if the username on the remote machine is the same as on the local machine, you can leave off user@ )
Executing commands remotely
Also, pretty straightforward...
Regular Command-Line commands
ssh user@MACHINENAME "Command to be executed"
GUI (X11) commands
SSH can pass X11 windows through to remote machines.
If your remote system is not already configured for X11, you'll need to log into it & install xauth.
sudo apt install xauth
As an example: Say you want to open a graphical view of the status of a server. I currently use stacer for this task.
ssh -X user@MACHINENAME stacer
(You may have to enable X11 Forwarding...)
Priveledged Remote Commands (needing root)
If you want to execute a command remotely that requires sudo, you'll have to add a -t to the command line or else sudo with tell you where to go.
ssh -t user@MACHINENAME "Command to be executed"
This is because sudo intentionally will NOT run without a local terminal session.
Another option is to enable root login via ssh.
WARNING!!! This may be a security risk!
vi /etc/ssh/sshd_config
and change:
#PermitRootLogin prohibit-password
to:
PermitRootLogin yes
Transferring files
There are at least 3 ways you can securely transfer files using SSH (via the SCP command)
From the local machine to a remote machine:
scp FileName user@MACHINENAME:Destination
From a remote machine to the local machine:
scp user@MACHINENAME:FileName Destination
From a remote machine to another remote machine:
scp user@MACHINENAME:FileName user@OTHERMACHINENAME:Destination
Starting to see a pattern?
As a bonus, RSYNC will use SSH as a transport layer.
Port forwarding (AKA Tunnelling)
Working on this part...
Troubleshooting
(somebody remind me to clean this crap up & make it easier to follow...)
If you get crap like:
Warning: the ECDSA host key for '<snip>' differs from the key for the IP address '<snip>' Offending key for IP in /home/<snip>/.ssh/known_hosts:14 Matching host key in /home/<snip>/.ssh/known_hosts:12 Are you sure you want to continue connecting (yes/no)?
or maybe:
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ @ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @ @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY! Someone could be eavesdropping on you right now (man-in-the-middle attack)! It is also possible that a host key has just been changed. The fingerprint for the RSA key sent by the remote host is SHA256:'<snip>' Please contact your system administrator. Add correct host key in /home/user/.ssh/known_hosts to get rid of this message. Offending RSA key in /home/user/.ssh/known_hosts:102 remove with: ssh-keygen -f "/home/user/.ssh/known_hosts" -R '<snip>' RSA host key for '<snip>' has changed and you have requested strict checking. Host key verification failed.
when you try to ssh to a machine...
sudo ssh-keygen -f ~/.ssh/known_hosts -R HOSTIP
Messages like:
Warning: the RSA host key for '<snip>' differs from the key for the IP address '<snip>' Offending key for IP in /home/user/.ssh/known_hosts:102 Matching host key in /home/user/.ssh/known_hosts:103 Are you sure you want to continue connecting (yes/no)?
mean that you have an extra entry in your known_hosts file & indicates the line you want to delete...
If you see:
Failed to add the host to the list of known hosts (/Users/USER/.ssh/known_hosts).
Check permissions & ownership on that file...